- Sustainability
- Social
- Information Security
Information Security
- Sustainability
- Social
- Information Security
Information Security
Information Security
Hyosung actively bolsters its information security system and engages in a variety of activities to prevent the disclosure of sensitive company data.
Information security issues are constantly evolving as a result of changes in business and information technology. Hence, companies are responsible for actively strengthening their information security systems in order to effectively address evolving information security threats. Considering that information is not a tangible asset, information itself has value, and the nature of conducting business while sharing information within and outside the organization, it is essential to identify information flow in the course of work and identify information security risks. Moreover, it is crucial to pinpoint precisely where risks may occur.
Hyosung has established information security regulations and operating standards to prepare for information security risks resulting from external cyber terrorism or internal data leakage, as well as a system to monitor their compliance. In addition, we implement various measures to prevent the leakage of sensitive data, such as reviewing security logs and deploying multifunction devices with security solutions.
-
Information security policy and system
Information security policy and system 

- 1. An information security policy that specifies the responsibilities and roles of each organization is developed, approved by the company's top management, and disseminated throughout the organization in order to reduce the risks associated with information security.
- 2. A planning, approval, execution, and monitoring process is established to effectively carry out the risk mitigation activities outlined in the information security policy.
- 3. Changes in domestic and international laws and requirements pertaining to information security are monitored and reflected in information security policy and system.
-
Information security organization (holding company)
- 1. As an organization committed to information security, there is a security team consisting of a Chief Information Security Officer (CISO) with more than five years of experience in the field of information security and information security staff at the entry level.
- 2. Each business site has a business site security manager and each team a team security manager, and they work together to ensure that the information security policy and activities are effectively implemented in the field. Security managers serve as a conduit for receiving information security issues and incidents from the field.
- 3. For issues requiring support from related departments, we convene a (temporary) information security council meeting comprised of HR, general affairs, legal affairs, and IT departments. Here, the roles and responsibilities of each department are clearly defined so that they can work in cooperation.
-
Information security organization (business company)
- 1. A CISO and a security manager are designated to oversee both information security and other responsibilities, and these individuals collaborate with the security team of the holding company to ensure that the holding company's information security policy is effectively implemented within the business company.
- 2. Each business site has a business site security manager and each team a team security manager, and they work together to ensure that the information security policy and activities are effectively implemented in the field. Security managers serve as a conduit for receiving information security issues and incidents from the field.
- 3. For issues requiring support from related departments, we convene a (temporary) information security council meeting comprised of HR, general affairs, legal affairs, and IT departments. Here, the roles and responsibilities of each department are clearly defined so that they can work in cooperation.
-
Increasing awareness of information security among employees
Increasing awareness of information security among employees Type Target Cycle Announcement via email/internal bulletin All employees Occasional Occasional All employees Daily Offline manager training Information security managers at each department Yearly Online training for all employees All employees Yearly - 1. All employees are subject to online information security training which is conducted each year, and security managers at each department receive offline training annually. Internal bulletin and groupware pop-ups are used to disseminate the updated information security policy and security incident prevention regulations.
- 2. We promote awareness-raising activities to prevent security incidents, such as simulating email attacks every six months to train on how to respond to suspicious emails.
- 3. In order to increase awareness of information security, new hires and prospective retirees are required to sign a pledge to protect sensitive data.
-
Privacy
- 1. We continuously monitor the status of amendments to laws concerning privacy and respond accordingly.
- 2. We provide personal data handlers with privacy training once a year.
- 3. We strive to ensure the security of personal data held by our organization by maintaining access logs of such data and performing periodic audits to determine whether data whose retention period has expired has been deleted.
-
Designation and management of protected areas
- 1. Offices, research institutes, factories, etc., are designated as protected areas where unauthorized access is restricted, and access records are managed by installing an ID card or fingerprint-based access system at the doors.
- 2. Areas that require particularly stringent access control (e.g. computer rooms) are designated as controlled areas, with security guards deployed or surveillance cameras installed.
- 3. The unauthorized removal of company property or introduction of personal computers or storage media without prior authorization is prohibited.
-
Regular security surveillance and response to security incidents
- 1. In order to prevent cybersecurity incidents such as hacking, the security team and dispatched personnel from companies specializing in security control conduct 24-hour surveillance.
- 2. Information on domestic and foreign infringement incidents is input into Hyosung's security equipment to prevent similar occurrences, and anomalies are promptly identified through real-time monitoring.
- 3. A security incident response procedure and an emergency communications network are established to provide a system for responding quickly to security incidents in accordance with the established procedures.
-
Access control
- 1. Hyosung prevents unauthorized access by employing distinct access control policies for general users and system administrators.
- 2. When accessing the internal business system from outside the organization, such as when working from home or traveling, the communication section is encrypted and protected by VPN. Risk of cybersecurity incidents resulting from account data leakage is also reduced by implementing two-factor authentication with a unique one-time password (OTP).
- 3. In addition to operator ID, IP address restrictions and OTP authentication are implemented for server access to the information system, and all server-executed commands are recorded to prevent security incidents and quickly identify their causes.
-
Integrated log management
- 1. Logs generated by security solutions such as servers, network equipment, application logs, and firewalls are managed cohesively in order to prevent log loss and tampering and securely store logs.
- 2. Using the security information and event management (SIEM) solution, an alert is immediately triggered if an action exceeds the threshold value, followed by an immediate action. The SIEM rule and threshold value are periodically adjusted.
-
Security review and vulnerability assessment
- 1. Risks are minimized through security review procedures when introducing and changing information systems.
- 2. Even when network control policies are modified, such as when the web server is opened to the public, security is reviewed to prevent unauthorized access.
- 3. Information systems such as servers, network equipment, and application programs are inspected annually for security flaws, and any found are patched.
-
Safe PC use
- 1. Security programs such as antivirus are installed on the user's computer to protect against ransomware and other malicious code attacks.
- 2. The company blocks access to malicious IPs and URLs and restricts access to non-work-related websites such as P2P lending sites.
- 3. In addition, media control programs are used to prohibit the unauthorized copying of files stored on PCs to USB storage devices, and data loss prevention solutions are employed to prevent the unauthorized disclosure of sensitive data such as trade secrets.
-
Centralized document management system
- 1. Hyosung reduces document search times and eliminates document sharing and collaboration restrictions. In 2019, we implemented enterprise content management (ECM) to support advanced work process and eliminate the possibility of information leakage during document distribution. We have thereby established a consistent document security policy across all business sites, ensuring visibility throughout the document distribution process.
- 2. Even when working from home, we provide an environment in which employees can access the centralized document management system and utilize work-related documents with ease, thereby enhancing the efficiency of telecommuting.
- 3. We apply the "Need-To-Know" principle to restrict access to documents by unauthorized personnel, and provide a function that enables the specification of additional access rights.
- 4. When taking documents out of the company, a control procedure is implemented to prevent unauthorized removal.
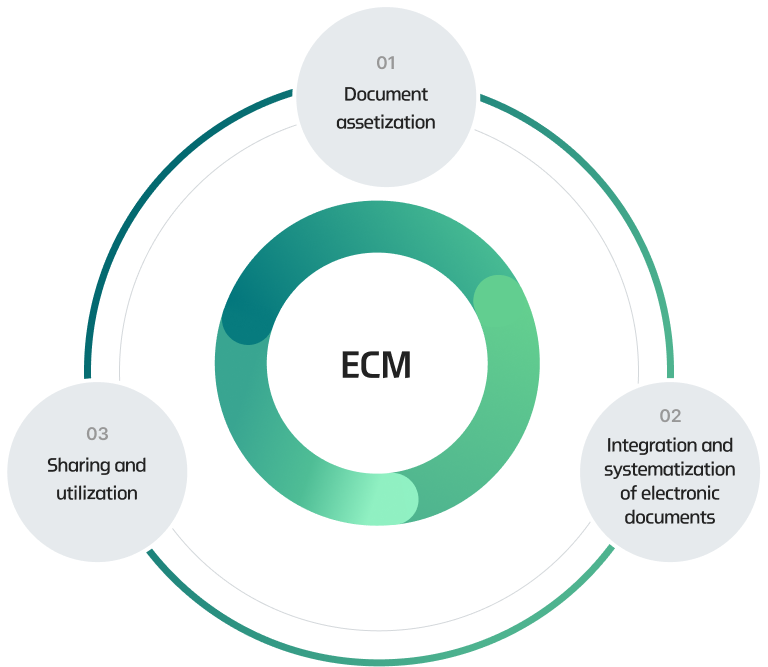
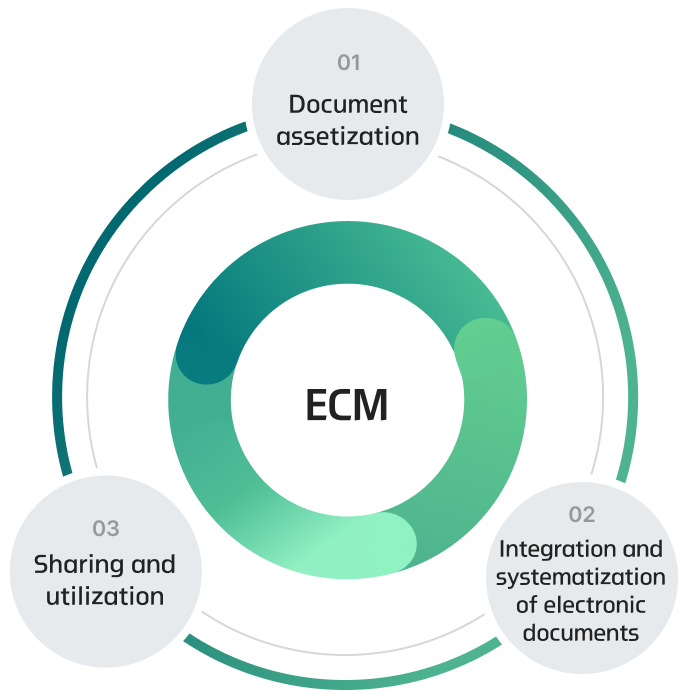
- Facilitating collaboration through document authenticity management
- Assetization of documents and/or content
- Accumulation of core capacity and competitiveness
- Enhancement of security and transition methods
Controlling document saving and exports
- Implementation of document export control system
- Implementation of role- and document-level access control
- Implementation of document monitoring system
-
PC saving control
- Unable to store critical documents on PC
- All documents are managed in the ECM system
- Elimination of the potential for document loss
-
Export control
- Only approved documents are exportable
- Dual management of outgoing channels (e.g. USB, e-mail, printing)
-
Document class classification
- Definition of class depending on importance of a document
- Definition of search and access rights by document class
-
Access control by role
- Definition of task scope for each user role
- Prevention of uncontrolled document access sources for system operators
-
Log analysis
- History (log) management over all document-related actions
- Periodic sampling of key departments/workers and abnormal users, identification of abnormal behaviors/measures
-
Establishment of an external cooperation system
- 1. Hyosung has partnered with the Korean Association for Industrial Technology Security (KAITS), which offers member companies services such as conferences, newsletters on the newest security trends, security training, and security consulting. Through continuous exchange and cooperation with KAITS and its member companies, we intend to prevent technology leakage, improve the level of response to security incidents, and implement security policies that are consistent with government policies and global trends.
- 2. In 2021, the Minister of Trade, Industry, and Energy presented us with a commendation on "Industrial Technology Protection Day" in honor of our efforts to protect industrial technology.